Imagine waking up to the aroma of freshly brewed coffee, your thermostat perfectly adjusting the temperature, and lights illuminating your path as you step out of bed. This isn’t just a futuristic dream; it’s a reality in many homes today! Thanks to IoT smart devices, convenience is at our fingertips. But the impact of IoT goes beyond our homes. It’s reshaping industries too. The term “Industry 4.0” emerged in 2011, heralding a new era focused on IoT and smart manufacturing. Fast forward ten years, and robotics has taken center stage, with companies leveraging automated systems to boost production capabilities.
The global IoT market is projected to exceed $5 trillion within the next decade. The number of connected devices has skyrocketed from 8 billion in 2019 to 16 billion in 2023, with estimates indicating it could reach 40 billion by 2030. This remarkable growth highlights an increasing dependence on smart technologies across various domains, including homes, businesses, and urban environments. These technologies encompass a wide range of applications, from smart speakers and CCTV cameras to advanced industrial control systems.

However, the IoT hasn’t scaled as quickly as expected.
What’s impeding its growth?
The proliferation of connected devices, along with the advancement of the complexity in IoT use cases (such as autonomous systems and transportation), creates opportunities for multiple players of the value chain. But it also creates the risk of vulnerabilities that could have catastrophic consequences. For example, now an average vehicle can have millions of lines of code from 150+ vendors, broadening the feature set and improving user experience, but also expanding the automotive cyber-attack surface.
A McKinsey survey suggest that 32% of the enterprises find cybersecurity as an impediment to adopt IoT devices into their ecosystem.
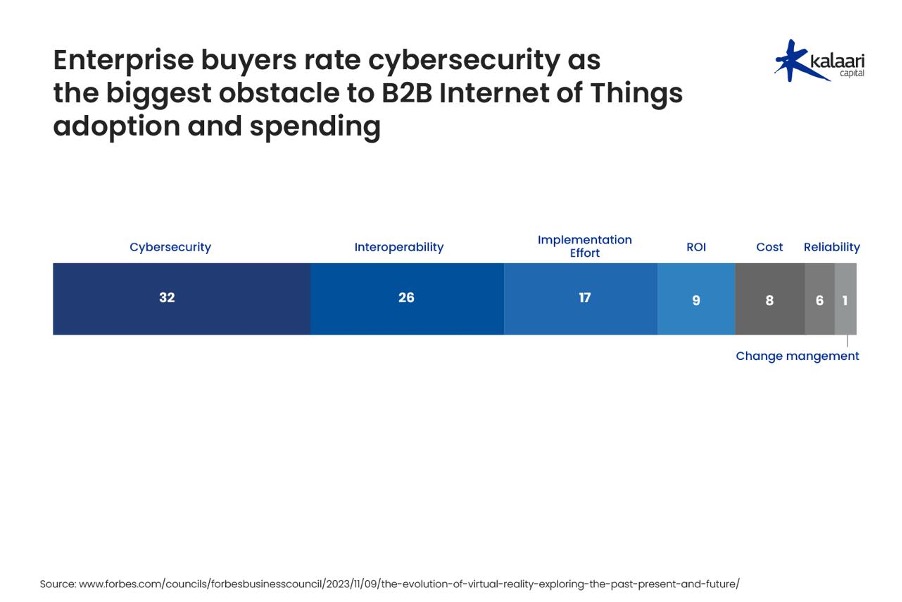
The risk profiles of many IoT systems are significantly higher than those of traditional enterprise IT systems, primarily due to their direct influence over physical operations. For instance, in industrial contexts, vulnerabilities can range from critical information leaks to damaging industrial control systems, ultimately compromising company operations. Consider a scenario where an attacker infiltrates the network of an automotive supplier and alters the machine settings for a brake component without detection. Such manipulation could result in brake failure under load, posing severe safety risks. The resulting damage—both tangible and intangible—can be exceedingly difficult to quantify, highlighting the unique and profound risks associated with IoT systems in industrial and consumer applications.
Conventional security measures for IoT do not provide the secure and seamless experience that users expect. Many IoT buyers have noted a lack of multilayered security in the current designs of IoT solutions. This deficiency creates vulnerabilities that necessitate frequent over-the-air updates and patches, which are often challenging to implement reliably. Compared to enterprise IT, the design of IoT solutions falls short in terms of security assurance, testing, and verification.
Hence, there is a pressing need for robust IoT security solutions to address these critical gaps and enhance overall system integrity.
The Current IoT Security Landscape:

- A report by Zscaler indicates that there has been a staggering 400% increase in IoT malware attacks year-over-year. The manufacturing sector has been particularly affected, accounting for 54.5% of all blocked IoT malware attacks, with an average of 6,000 weekly attacks across monitored devices.
- There’s a huge need for IoT security in automotive industry – Just in 2023, 50% of all the attacks were tagged as High or Massive impact incidents, which has doubled from 2022. Given the growth in the adoption of autonomous vehicles and government emphasis on regulations, the global automotive cybersecurity market is expected to reach $16.5Bn in the coming decade.
- In 2023, IoT malware attacks in the education sector surged by nearly 1000%, driven by unsecured and shadow devices that expose personal data and create vulnerabilities for students and administration.
Common IoT Security Attacks Observed

Notable cyber-attacks in the IoT Environment:
- Mirai Botnet Attack (2016)
The Mirai botnet is one of the most infamous IoT attacks, which exploited poorly secured IoT devices like cameras and DVRs. In October 2016, it was used to execute a massive Distributed Denial of Service (DDoS) attack against Dyn, a major DNS provider. This attack caused widespread outages for major websites, including Twitter, Netflix, and CNN, demonstrating the potential of IoT vulnerabilities to disrupt internet services on a large scale.
- Colonial Pipeline Ransomware Attack (2021)
In May 2021, the Colonial Pipeline, responsible for transporting nearly half of the East Coast’s fuel supply, suffered a ransomware attack. Although the attack primarily affected IT systems, it led to a shutdown of operations that resulted in fuel shortages and panic buying across several states. The incident underscored the vulnerabilities of OT systems within critical infrastructure.
- JBS Foods Ransomware Attack (2021)
In late May 2021, JBS, one of the world’s largest meat processing companies, was targeted by a ransomware attack that forced it to halt production at several facilities in North America and Australia. The attack disrupted operations significantly and highlighted the risks posed by cyber threats to food supply chains.
- Oil India Limited Attack (2022)
In April 2022, Oil India Limited faced a cyberattack that led to ransom demands exceeding ₹57 crore (~ $7 million). Although production systems were reportedly unaffected, this incident highlighted ongoing threats faced by critical infrastructure sectors in India.
Key Security Models and Strategies to Secure the IoT environment
Here’re some key models and frameworks adopted by the industry to secure their connected devices.
- NIST Cybersecurity Framework (CSF): It serves as a foundational structure for organizations to develop or improve their cybersecurity programs. It is adaptable across different sectors and provides a flexible, technology-neutral approach to managing cybersecurity risks. The framework is organized into five core functions: Identify, Protect, Detect, Respond & Recover. To specifically address IoT security, NIST has developed the IoT Security Maturity Model (SMM), which helps organizations assess their security practices related to IoT devices. The SMM provides a structured approach for organizations to determine their current security maturity and identify areas for improvement.
- Zero Trust Architecture (ZTA): It operates on the principle of “never trust, always verify,” meaning that no device or user, whether inside or outside the network perimeter, is trusted by default. Key principles of ZTA are,
- Assume Breach: Operate under the belief that breaches are inevitable, prompting stringent security measures for all devices and users.
- Continuous Verification: Every access request is continuously verified based on user identity, device health, and contextual factors, ensuring timely re-evaluation of access rights.
- Least Privilege Access: Grant minimal permissions necessary for users and devices to function, limiting potential damage from breaches.
- Micro-Segmentation: Create isolated network zones to restrict lateral movement by attackers, confining breaches to limited areas.
- Comprehensive Logging and Monitoring: Log and monitor all network interactions to detect suspicious activity and provide visibility into device behaviours.
By adopting a Zero Trust Architecture in IoT security, organizations can significantly enhance their defences against cyber threats, ensuring that every device and user is continuously verified, and that access is strictly controlled based on real-time assessments of risk.
- IoT Security Metamodel (IoTSM): Developed for smart cities, the IoTSM combines various security aspects such as authentication, device management, and secure communication. It provides a comprehensive framework to address the unique security challenges of IoT environments by integrating multiple security processes into a cohesive model.
- Industrial Internet Security Framework (IISF): Published by the Industrial Internet Consortium (IIC), this framework outlines best practices and guidelines for securing industrial IoT systems. It focuses on risk management, secure design principles, and operational practices that help organizations implement robust security measures across their IoT deployments.
- Defense-in-Depth Strategy: This approach involves implementing multiple layers of security controls throughout the IoT architecture. By combining physical security, network defenses, endpoint protection, and application security measures, organizations can create a robust barrier against potential threats. Each layer serves as a backup to others, enhancing overall resilience.
- Threat Modelling Frameworks: Like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) help organizations identify potential threats specific to their IoT applications. By categorizing risks and implementing appropriate mitigations at various system levels, organizations can enhance their overall security posture.
Key point to note here’s the frameworks that are employed currently complement each other by providing additional strategies tailored to the unique challenges in the IoT security. Implementing a combination of these approaches can significantly enhance an organization’s ability to protect its IoT assets against evolving cyber threats.
Market Map: Global IoT Security Players
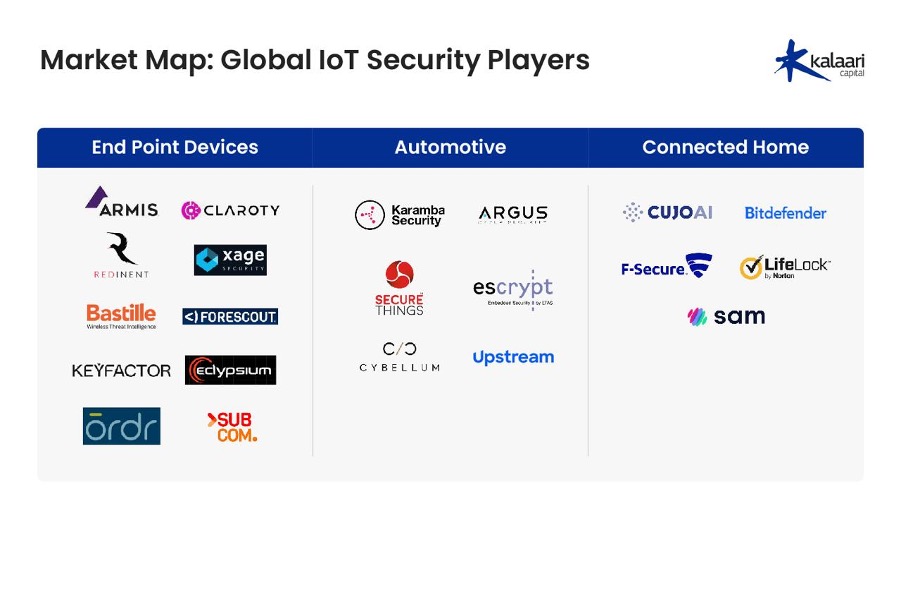
India’s cybersecurity landscape is witnessing a significant transformation, with an increasing number of startups emerging, particularly in the IoT security sector. While the market has traditionally been dominated by global corporations, innovative companies such as Redinent, Subcom, and SecureThings are making notable strides. These startups are distinguishing themselves from established players through their robust technology stacks and distinctive offerings, enabling them to outperform their larger counterparts in this competitive field.
Future of Cyber Security in IoT Environment
Cybersecurity plays a crucial role in fostering trust and facilitating the integration of IoT networks. As the proliferation of IoT devices amplifies cybersecurity risks—spanning both digital and physical domains—the convergence of IoT and cybersecurity solutions is essential for accelerating IoT adoption. By 2030, the TAM for IoT suppliers are projected to reach $500 billion. Notably, four key sectors—manufacturing and industrial, mobility and transportation, healthcare, and smart cities—will account for over 65% of this market. However, significant challenges persist, including heightened expectations for privacy and digital trust from consumers, fragmented decision-making processes regarding IoT and cybersecurity, and the absence of industry-specific security architectures during the design phase.
If cybersecurity risks are effectively managed, companies could increase their IoT investments by an average of 20% to 40%, translating to an additional $100 billion to $200 billion in spending. This increase not only enhances the TAM for existing applications but also fosters an environment ripe for innovative use cases to emerge. As a result, IoT suppliers could see an additional value creation of $25 billion to $50 billion, pushing the combined TAM for IoT suppliers to between $625 billion and $750 billion across various industries.

To address concerns regarding digital trust and privacy, the convergence of IoT and cybersecurity must focus on enabling new use cases while enhancing existing ones. This approach will likely drive the adoption of higher security standards within the IoT industry, influenced by government regulations. Moreover, tailored solutions that cater to specific industry needs will be more effective than generic approaches, ensuring comprehensive coverage across the entire technology stack rather than applying superficial fixes.
This scenario presents a unique opportunity for integrated solution providers to unify the currently fragmented landscape of IoT and cybersecurity services. Nevertheless, it is important to recognize that this market will not favour a single dominant player; instead, collaboration among various stakeholders will be vital in mitigating risks associated with IoT. By working together, these entities can maximize the potential for IoT to enhance various aspects of daily life while also positioning themselves to benefit from this evolving technological landscape.
Kalaari’ Outlook
The cybersecurity landscape can be categorized into seven key areas: Network Security, Application Security, Operational Technology (IoT) Security, Data Security, Identity and Access Management, Incident Response, and Governance, Risk Management, and Compliance (GRC). While established players have built robust foundations across six of these categories, IoT security remains notably underdeveloped. As industries rapidly adopt connected devices, a significant gap in cybersecurity for IoT is emerging. As previously mentioned, effective cybersecurity solutions will be crucial in facilitating IoT adoption across various sectors.
In India, the market is gradually embracing security practices within operational technology. Several critical areas require immediate attention:
- Asset Discovery: Many enterprises lack awareness of the IoT assets present within their facilities. This oversight can lead to vulnerabilities that facilitate breaches. There is a pressing demand for organizations to identify their assets and their specific locations.
- Streamlined Compliance: Organizations need comprehensive evaluations of their compliance status and security posture. As certifications become increasingly essential, detailed reporting will be vital.
- Zero-Day Vulnerabilities: Rather than passively monitoring device network traffic, proactive probing using a Zero Trust architecture can provide a clearer understanding of the security status of IoT endpoints.
- Remediation: Alongside identifying risks, organizations require solutions for implementing remediation strategies. Given the sensitive nature of security operations, many organizations prefer to manage these implementations internally; however, this could change if solutions are offered with adequate support and guidelines.
- Integrations: Integrations with existing security solutions including SIEMs and SOCs are essential for IoT cybersecurity solutions because they enhance visibility and context around connected devices, enabling better monitoring and threat detection across diverse environments. This integration allows for a more cohesive security posture, facilitating automated responses to incidents and reducing the overall risk of vulnerabilities within the IoT ecosystem
AI Automated Workflow
The aforementioned areas can be greatly enhanced through AI by improving threat classification and identification, automating security workflows, and enabling proactive threat detection. It can also facilitate key integrations that automate security playbooks and ensure seamless end-to-end connectivity across systems. Startups should focus on leveraging relevant data along with the growing public databases to develop tailored models that automate workflows related to asset discovery, threat intelligence, remediation efforts, and reporting.
The Make in India initiative emphasizes the development of homegrown IoT security solutions to enhance national security, particularly in defence and government procurement. By building in local capabilities, India can build a resilient digital infrastructure that meets both current and future challenges in the IoT cybersecurity landscape.
If you’re an early-stage founder building in cybersecurity domain, we want to hear from you. Reach out to us at pitch@kalaari.com – let’s explore how we can shape the future of cyber security ecosystem together.








